Users need two-factor authentication for more reliable protection of their accounts: while each individual authentication method is vulnerable, two (or more) of them used together make account-takeover a lot more difficult.
In this post, I cover the available multi-factor authentication options, give you the pros and cons of each, and recommend the most secure ones for you to keep your accounts safe.
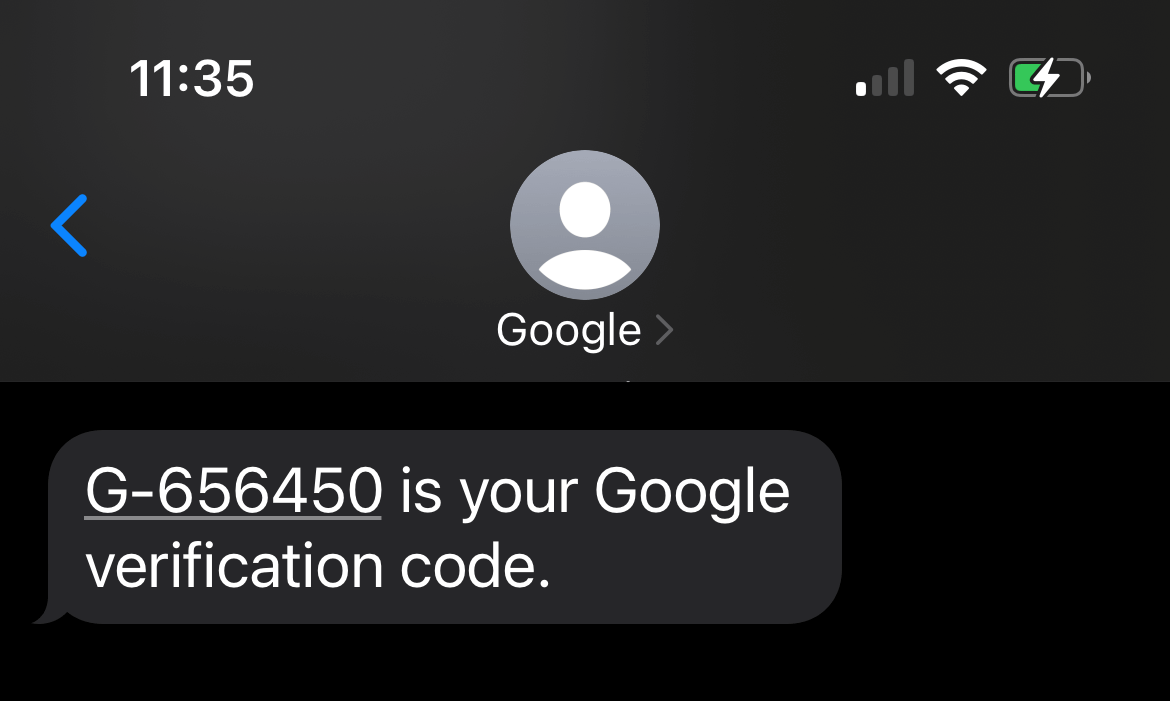
One-time codes delivered by SMS, email or voice call
One of the most common two-factor authentication mechanisms for sign-in validation are one-time codes. These are usually sent in a text message to the phone number specified during registration. Email can be used for it as well but is less popular. Major services usually also provide the option of a voice call to the phone number specified upon registration.
Whatever the delivery channel used, the idea is the same: to verify your ability to get access to some other account or phone number you specified when signing up for the service. Thus, if someone steals your password while having no access to your phone, this protection will work just fine.
But this two-factor authentication mechanism has its downsides. If email is used to confirm the login, and the password for logging into it is the same as for the account you’re trying to protect, you’ll get very limited extra security. An attacker who knows the account’s password is certain to try that password to sign in to your email too — thus getting the one-time validation code.
Validation through phone number — whether by SMS or voice call — has a different problem: it’s easy to lose access to it. Sometimes users simply forget to top up their phone account, or they lose the phone or change the number.
It’s also not uncommon for criminals to persuade the telecom operators to give them a SIM card with the victim’s phone number, thus getting access to validation codes. Also, the text messages can be intercepted — such cases were already reported.
Summary: this two-factor authentication option gets the job done, but to protect the most valuable accounts — especially those related to finances — it’s better to use something more reliable.
Password as second factor
Sometimes the password is not the first but the second factor. This is what messengers often do: by default, to sign in it’s enough to enter the one-time code from the SMS. The password is usually optional. Optional but necessary, if you ask me. It will safeguard you against a whole bunch of potential problems in one go.
Most importantly, it will protect your correspondence from accidental loss of access to the phone number you used to register in WhatsApp or Telegram. Suppose you changed your main phone number and put your old SIM card into a drawer and didn’t pay for it for a long time. The operator will resell your number after a while, thus enabling the new owner to sign in to the messenger under your name — unless it’s additionally protected with a password, of course.
And sure enough, the password will give your messenger account at least some protection from hijackers who have — one way or another — gained access to your phone number.
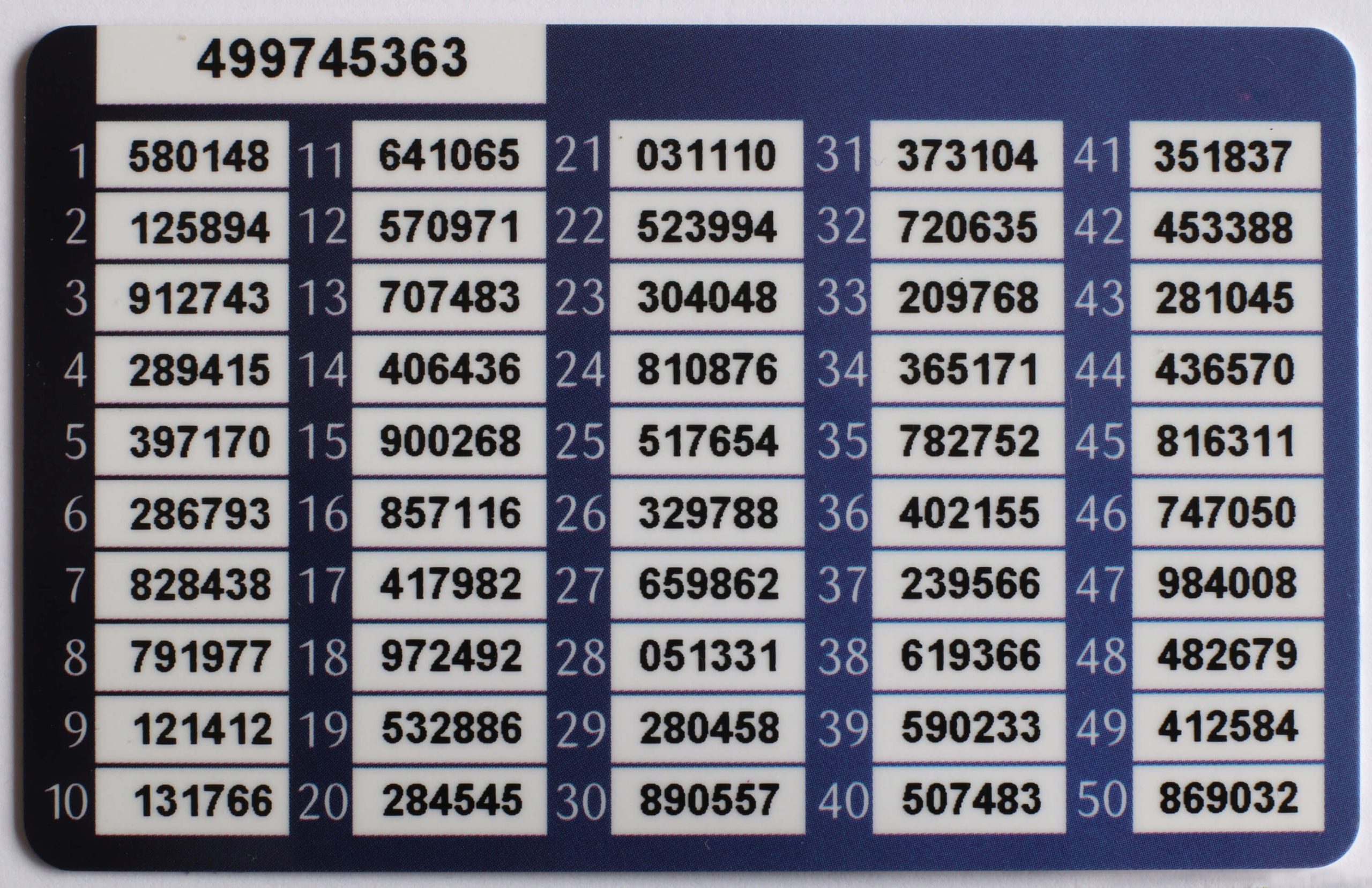
Pre-generated list of one-time codes
Another option you can come across is a list of pre-generated one-time codes. Banks sometimes issue such lists to their clients to confirm transactions, while some internet services (such as Google) allow using them for account recovery.
This can be considered a reliable mechanism: such codes are transmitted to the user extremely rarely, so there’s a minimum of opportunities for interception. The codes are random, meaning they’re unique, so guessing them is almost impossible.
But there’s the storage issue: if attackers manage to steal your list of pre-generated codes, hijacking your account or stealing money from it will be extremely easy.
Therefore one-time confirmation codes should be stored in a strongbox or in its electronic counterpart. For example, there are encrypted notes in Kaspersky Password Manager. If you save the list of one-time codes in these notes, they’ll be securely protected, provided, of course, that you set a good and unique master password for Kaspersky Password Manager itself.
However, the main inconvenience of this authentication method is that if you need verifications often, you’ll quickly run out of your pre-generated codes. Which means you’ll have to generate and save more and more new ones. If maintaining multiple accounts, you’ll easily get confused by all those lists. Therefore, pre-generated codes as the main authentication method have been replaced by codes generated upon request — just as you need them.
One-time codes from an authenticator app
“On the fly” generation of one-time codes is done by authenticators. These can sometimes be stand-alone devices with a small screen that displays the current code — some banks give such authenticators to their clients.
But these days special authenticator apps run on smartphones are more popular than stand-alone devices. We have a number of posts about them:
- Authenticator apps and how they work
- Best authenticator apps for Android, iOS, Windows and macOS
- Authentication with one-time codes: pros and cons
- What to do if you lose your phone with an authenticator app
So if looking for information on how this authentication method works, how to select an authenticator app, and what to keep in mind once you have one, follow the links above. Meanwhile here, I’ll just briefly state that authenticator apps offer an optimal trade-off between convenience and security — making them more and more popular.

Google Authenticator: the most well-known but by far not the only authenticator app out there
Biometrics: fingerprint, face or voice
Not so long ago, for most people, biometric authentication was something exotic. However, things changed rather quickly: most smartphones now have the ability to authenticate either by fingerprint or face recognition — and it comes as no surprise.
But some biometrics methods can strike you as unusual: voice-, iris-, walk- and typing habit-based authentication. As to the most original ones, we could recall research into odor-based authentication (though it doesn’t work too well)!
Biometric authentication has a couple of serious drawbacks. First: all the characteristics it relies upon are the user’s permanent properties. You can change a compromised password — you can even do it multiple times for safety’s sake. But a registered fingerprint can be changed only a limited number of times — the attempts can literally be counted on the fingers of two hands.
The second important issue consists in the fact that biometric data is extremely sensitive — both for being unalterable and because it allows not only to authenticate a user, but also to identify a person. So collection and transfer of this data to digital services should be treated with extreme caution.
This is why biometric data is normally used for local authentication: stored and processed on the device to avoid transmitting it anywhere. For remote biometric authentication, the digital service would have to trust the device vendor, which services normally don’t want to do. The net result is this: only Apple has a full-value remote biometric authentication mechanism, because the company is in full control its ecosystem — from software development through to device fabrication.
But biometric authentication has one important advantage overriding its downsides. If properly implemented, it makes the users’ life much simpler: no more typing — just press your finger to the sensor or show your face to the camera. And it’s fairly reliable too — again, if properly implemented.
Location
One more user authentication type is location. You don’t have to activate this method: it’s on by default. That’s why it usually goes unnoticed, with the person getting alerted only if it’s unsuccessful: that is, if a sign-in attempt comes from a location the service didn’t expect. In which case the service may require using an additional verification method.
Of course, location is not a very reliable authentication factor. Firstly, it’s not very unique: lots of other people can be at the same place at any given time. Secondly, it’s quite easy to manipulate, especially when speaking of IP-based location — not proper GPS geolocation. However, location can be used as one of the authentication factors, and many services do that.
Hardware keys FIDO U2F (aka YubiKey)
The authentication options described above have one major downside to them: they allow authenticating the user, but not the service. Which makes them vulnerable to the MitM (man-in-the-middle) attacks.
Attackers can build a fake page closely imitating the sign-in mechanism of the actual service. Once the user submits their login and password, criminals promptly use those to sign in to the real website. The verification code will be the next thing the user is asked to provide — and in no time it will be used to take over the victim’s account.
To deal with this kinds of threats, FIDO U2F keys were created, also known by the name of their most popular model — YubiKey. The main advantage of this method consists in the fact that, during registration, the service and the U2F key remember certain information that’s unique for each service as well as each user. Later during authentication, the service must send a specific request to the key, to which the key will respond only if this request is correct.
Thus, both sides of this communication understand whether or not it’s legitimate. Moreover, this authentication mechanism is based on open key cryptography, so the whole process is well protected against falsification, interception and similar threats.
One more advantage on top of that: even though the technology is rather sophisticated and uses hardcore cryptography “under the hood”, it all looks very simple on the surface — from the user’s point of view. Just plug the key into a USB socket (or hold to your smartphone — such keys often support NFC) and touch a sensor pad on the key with your finger to complete authentication.
Using U2F hardware keys is the most reliable authentication method available today and a recommended option for valuable accounts. That’s what they do at Google: all company employees have been using such keys for their corporate accounts for over five years now.
FIDO Passkeys: future present without passwords
It’s not easy but still possible to make all employees within your organization use hardware keys for authentication. Yet the method is hardly suitable for millions of regular internet users. Ordinary folks are often annoyed with the mere idea of two-factor authentication, let alone paying money for some special equipment.
That is why the same FIDO Alliance, the creator of U2F keys, has developed a new authentication standard that uses “passkeys” in place of passwords. In simple terms, the technology is about the same as with U2F keys, except you don’t need any special device to store the authentication data.
You can store passkeys basically anywhere — smartphone, computer, browser’s user profile or — the old fashioned way — a USB key. You can choose to synchronize them through the cloud or not to synchronize them at all, if opting for the unique passcode mode.
This long list of storage options makes passkeys somewhat less secure, obviously. Just how much less — that depends on what combination of equipment and services you use.
To compensate, users get this valuable advantage: passkeys don’t complement account passwords, they replace them. On top of that, such authentication is still a multi-factored one: in addition to owning a device used to store your passkeys, you have to validate sign-in either using biometrics (if your gadget supports it) or PIN to unlock your device. As you can see, you cannot go completely without passwords in some cases, but at least passkeys greatly reduce their number.
The initiative’s key problem is that so far it’s like a patchwork quilt. Different platforms and services use very different approaches to data storage, user authentication and security as a whole. So instead of just one method, a number of different ones are used, varying greatly in terms of reliability.
So it would be a bit premature to switch to passkeys completely. But you can experiment with them already: a while ago Google announced full support of passkeys by Google accounts, so if interested, anyone can see how it works in real life.
Which two-factor authentication methods are better, and other things to remember
To conclude, the key points:
- In 2023, two-factor authentication is no longer a luxury but rather a vital necessity. Use it wherever possible.
- Any two-factor authentication method is way better than none at all.
- Authenticator apps are optimal for two-way authentication.
- A FIDO U2F hardware key — Yubico YubiKey, Google Titan or other — is an even better option. Especially for high-value accounts.
- You can experiment with passkeys already, but it seems a bit early to fully embrace the technology.
- Therefore, it’s still vital to use passwords with care: go for complex ones, don’t reuse them for multiple services, and keep them safe using a password manager.
- And of course, don’t forget that most two-factor authentication methods (other than U2F and passkeys) are vulnerable to phishing. Therefore, use a reliable solution that automatically removes this threat, such as Kaspersky Premium.